
The vulnerability assessment tools are one of the essential tools in IT departments and information security groups to verify vulnerabilities that appear every day and thus leave an entry hole in the criminal organization.
The vulnerability scanning tools help detect security holes in applications, operating systems, hardware, and network systems. Hackers are actively looking for these breaches to use them to their advantage. Vulnerabilities within a network need to be identified and corrected immediately to keep their attackers at bay.
Vulnerability scanners are the correct way to do this. With their continuous and automated tracking procedures, they can scan the network for possible breaches.
Whether on your Internet or any device, they would help IT and security identify the vulnerability and fix it manually and automatically.
Vulnerability scan tools have two different approaches to performing their routines, authenticated and unauthenticated scans.
In the latter case, a pen tester will scan as a hacker without reliable access to the corporate network. This type of verification will help organizations identify gaps that will allow hackers to penetrate the system without trusted permissions.
While in the first case, the same tester registers as a user and scans the network, showing the vulnerabilities available to a hacker who is now disguised as a trusted user.
The best web vulnerability scanner on the market should allow you to perform authenticated and unauthenticated scans to identify and correct network and other vulnerabilities that have been identified.
Here are the top 5 vulnerability scanning tools, according to GBHackers, available on the market.
Table of Contents
Top 5 Vulnerability Scanning Tools:
OpenVAS Vulnerability Scanner
The OpenVAS Vulnerability Scanner is the vulnerability analysis tool that enables IT departments to scan servers and network devices, thanks to its comprehensive nature.

These scanners will look for an IP address and scan for any open services, checking open ports, incorrect settings, and vulnerabilities in existing installations.
After verification is complete, an automated report is generated and sent as an email for study and rectification.
OpenVAS can also be operated from an external server, providing the hacker perspective, identifying exposed ports or services and handling them on time.
If you already have an internal incident response or detection system, OpenVAS will help you improvise your network monitoring using Network Pentesting Tools and alerts as a whole.
Tripwire IP360
The Tripwire IP360 is a leading solutions vulnerability management market, enabling users to identify everything on your network, including local assets in the cloud and in containers.

Tripwire will allow IT departments to access your assets using an agent and fewer checks.
It also works in integration with vulnerability management and risk management , enabling IT administrators and security professionals to take a holistic approach to security management.
Nessus Vulnerability Scanner
The Professional Nessus Tenable is a tool for security professionals, caring fixes, software problems, removal malware, adware and misconfigurations in a wide variety of operating systems and applications.

Nessus creates a proactive security procedure that identifies vulnerabilities before hackers use them to break into a network. It also addresses remote code execution failures.
It applies to most network devices, including virtual, physical and cloud infrastructure.
Tenable was also mentioned as the Gartner Peer Insights Choice for vulnerability assessment in March 2019.
Comodo HackerProof
The Comodo HackerProof is another scanner vulnerabilities leader with robust features that allow IT departments to check their vulnerabilities daily.

PCI scanning options, drive-by attack prevention, and site inspection technology help scan next-generation sites.
In addition to these advantages, Comodo also provides an indicator for users to feel safe while interacting with you. This will reduce shopping cart abandonment, improve conversions, and generate revenue to a large extent. Not to forget its unique site inspector technology, which acts as the best counter for drive-by attacks.
Nexpose community
The Nexpose Community is a vulnerability assessment tool developed by Rapid7, it is an open-source solution that covers most of the network checks.
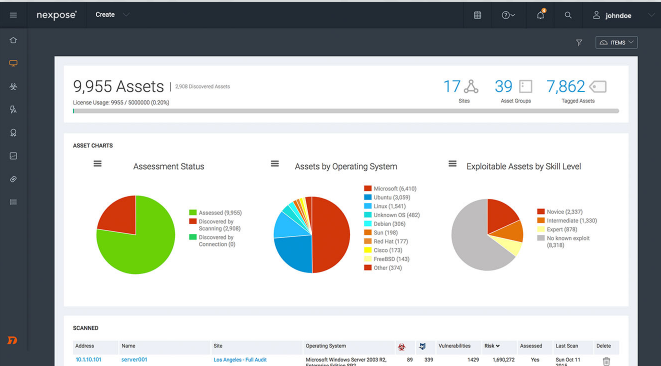
The versatility of this solution is an advantage for IT administrators as it can be incorporated into a Metasploit framework that can detect and scan devices as a new device accesses the network.
It also monitors real-world vulnerability exposures and, above all, identifies threat resources to develop accordingly fixes.
In addition, the vulnerability scanner also has a threat risk score ranging from 1 to 1000, providing security professionals with an idea to fix the correct vulnerability before it is exploited. Nexpose currently offers a one-year free trial.
I’m a passionate blogger for the last 5 years and love to play computer games. In my free time, I can write on internet services, telecom engineering, good and bad things about technology.
